Mobile apps are among businesses’ most valuable assets. Unfortunately, they’re also among businesses’ greatest security risks. These days, anyone with an iPhone, Android phone, iPad or Android tablet could put your entire company at risk due to an insecure or malicious application. If enterprise applications lack sufficient data security, businesses are taking huge risks. Everyone wants their data to be secure, however securing mobile devices poses a significant challenge.
What to do? The federal government’s National Institute of Standards and Technology (NIST) provides excellent advice in its publication “Vetting the Security of Mobile Applications.” (Download the free report here)
The report recommends that companies vet every single HTML5 mobile app before it’s deployed. And it says this shouldn’t be done in an ad hoc way, but rather via a strictly controlled process for every single app. With a strict process, security flaws in mobile apps can be caught and corrected, eliminating needless risks introduced by insecure apps. Using mobile development tools with integrated security frameworks make it easier to develop apps with mobile security.
Even before the vetting process, a company should develop a set of security requirements that specify, in the words of the report, “how data used by an app should be secured, the environment in which an app will be deployed, and the acceptable level of risk for an app.” For more information how to do that, get advice from the NIST report “Guidelines for Managing the Security of Mobile Devices in the Enterprise”
HTML5 Mobile App Security: The two-step process
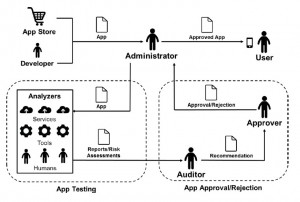
Once the requirements have been established, mobile app vetting should be a two-step process, the NIST says. The first step is app testing, to check for potential vulnerabilities. The second step is app approval or rejection.In the app testing process, all apps should be submitted to an administrator before being used in the business. The administrator is in charge of the testing and approval/rejection processes, and he or she should use one or more analyzers for checking the security of the app. These analyzers can be people, a testing service, or an automated tool, and they test the app against the set of security rules established by the organization.
After the testing is done, the analyzer creates a report about the app’s vulnerabilities, along with a risk assessment of those vulnerabilities.
In the approval/rejection process, the report and risk assessment are sent to an auditor, who determines whether the app meets the security requirements set out by the business. The auditor may do some independent research as well. He then creates report and recommendation, and sends it to an approver who makes the decision about whether to approve or reject the app. That decision is then sent back to the administrator, who lets approved apps into the organization, and ensures that rejected ones aren’t allowed in.
The following illustration, taken from the NIST report, shows the entire process in a nutshell.







Comment