There is little doubt that low-code and no-code platforms are growing in popularity. Gartner predicts, “That low-code and no-code tools will account for more than 65% of development activity,”
Low-code and no-code platforms are becoming increasingly important as more enterprises build their own mobile, desktop, and web applications. These platforms provide user-friendly visual interfaces and inbuilt components like drag and drop that allow citizen developers with minimal knowledge of programming languages to create applications that are highly functional and less prone to error.
Despite the growing adoption and fanfare of low-code platforms by tech leaders like the CEO of GitHub, Chris Wanstaff, who said, "The future of coding is no coding at all," it's important to address one of the biggest barriers to adopting low-code app development - security. According to recent research by Forrester, 59% of respondents said security is a top challenge when it comes to adopting a low-code platform.
For anyone, but especially for legacy enterprises, it's hard to break away from the traditional way of developing applications, especially considering that these companies have been doing in-house development for decades. That's why it's critical that no-code and low-code vendors address the concerns about security.
There are three main security issues with low-code platforms: IT visibility, permissions and controls, and third party integrations. In larger organizations, IT teams apply comprehensive security practices, precautions, and workflows to ensure application security. However, sometimes low-code applications created by business users do not follow the same guidelines.
Some possible solutions to these security concerns could be to consult IT or cybersecurity before deploying an app or to conduct an assessment or audit before choosing a low-code platform.


Low-code security is not well understood. Vendors who have invested in security admit that some of their customers have questions that remain unanswered. The number of companies using low-code is undoubtedly increasing. However, some are unknowingly relying on applications that can touch-sensitive corporate and customer data.
According to a study by Forrester, low-code is secure. Initial results show that building applications on low-code platforms is safer than using a traditional development approach. By low-code vendors taking responsibility for securing their platforms in their cloud and ensuring technical quality, many security [1]concerns like SQL injections or cross-site scripting are avoided [See footnote below for definitions].
Application security risks are higher when developers build parts of an application outside the native tools of a low-code platform. This risk is lowered for citizen developers who generally don't know how to write custom code. Low-code platforms designed for business users have fewer options for code customization, thus minimizing security issues.
[1] An SQL injection is when someone can see data they aren’t usually able to retrieve. For example: when an attacker interferes with queries that an application makes to a database. Cross-Site Scripting is when an attacker stores malicious code in data sent from a web search or contact form.
Companies pursuing digital transformation should take the following into consideration. First, carefully select vendors and partners. Second, select a platform based on the clarity and transparency of their security processes.
Questions to ask platforms are: What is the level of security awareness in the company? What tech stack are they using? Are they using security tools and SAST, DAST, IAST scanning? Asking these questions will help ensure that you are working with platforms that make security a high priority.
Keeping up to date with the latest security vulnerabilities doesn't have to be too time-consuming. Both professional developers and citizen developers should subscribe to information security sites to stay up to date and ensure that they are using the most secure and best practices when building applications. It's also important to invest in security awareness and hire security-savvy developers who are aware of potential threats and have the know-how to combat them.

IT teams and CISCOs recognize that low-code platforms tend to have fewer security vulnerabilities because less code needs to be written. However, it is still important to apply the same level of security testing as any traditionally developed software.

Most companies and developers view the low-code environment as a kind of black box whose workings cannot be seen. In many ways, this is true. The back-end activities on low-code platforms are not always visible to developers. Most low-code platforms have their inherent risks. For example, many vendors and their solutions do not undergo publicly viewable security audits, which could mean that security vulnerabilities remain.
Since most low-code development platforms don't give you admin access to their entire tool, you need to use auditing services to keep an eye on your security. Here are two examples of these types of automated tools for web applications:
OWASP (Open Web Application Security Project) has developed a solution called ZAP (Zed Attack Proxy). This service finds security vulnerabilities during the development and testing phases of an application. It covers scripting languages, automatic scanners, and plug-and-hack support. This solution can be used by both professional developers and citizen developers.
SonarQube is a solution analyzes over 20 programming languages for vulnerabilities. It covers cross-site scripting, Denial-of-Source (DoS) attacks, and SQL injection, among others.
Although the traditional development approach poses more security risks because the process involves writing custom code, organizations should still be vigilant when deciding to move to low-code platforms. By avoiding building parts of the application outside of the platform's native tools, promoting security awareness, and using testing tools, companies can get the most out of low-code platforms.
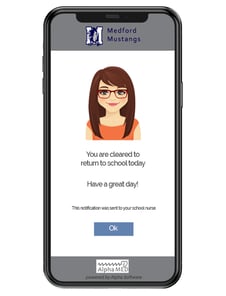

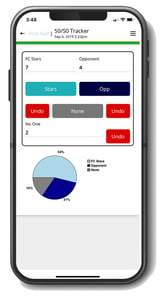
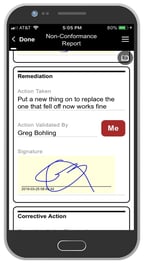

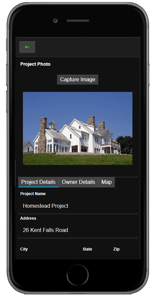
Alpha Anywhere is the best low code app development software for business. And we've made it easier than ever to get started with our new Alpha Anywhere Community Edition. This full-featured and FREE low-code development environment to help YOU succeed at building secure mobile apps. We also have a team of experienced app designers and developers who have produced tutorials on how to build and design a low-code mobile app for free.
The Alpha platform is the only unified mobile and web app development and deployment environment with distinct “no-code” and “low-code” components. Using the Alpha TransForm no-code product, business users and developers can take full advantage of all the capabilities of the smartphone to turn any form into a mobile app in minutes, and power users can add advanced app functionality with Alpha TransForm's built-in programming language. IT developers can use the Alpha Anywhere low-code environment to develop complex web or mobile business apps from scratch, integrate data with existing systems of record and workflows (including data collected via Alpha TransForm), and add additional security or authentication requirements to protect corporate data.
Alpha Software Corporation, based in Massachusetts, produces award-winning software that speeds mobile and web app development and deployment for business and IT. The core technology includes two components. Alpha Anywhere®, a full-stack low-code app development platform for building and deploying web and mobile apps. In just hours, Alpha TransForm® turns complex paper forms into powerful mobile forms that speed data collection.
Alpha Software is an InfoWorld Technology of the Year award winner, and scores near-perfect reviews from customers on crowdsourced review sites.
Customers rate Alpha Software highly for its speed of development, flexibility, offline apps, rich feature set and ability to scale predictably. For more information, visit https://www.alphasoftware.com/